
kras99 - stock.adobe.com
How to set up a VPN for enterprise use
VPNs are nearly ubiquitous, but does your organization know how to deploy one? Learn about use cases, requirements, deployment options and best practices for VPN deployment.
A virtual private network, or VPN, is a key technology used to boost internet security and enable safe remote access for users who need access to enterprise WANs and their resources. A VPN interconnects all kinds of users across all types of locations. Its features should be secure, user-friendly and flexible enough to traverse the cloud for a variety of platforms and use cases.
Before setting up a VPN, network architects should evaluate fundamental VPN principles, select features that best support their organizations' users, and consider best practices for security and secure remote network access.
How do VPNs work?
VPNs add a protocol layer, often called a tunneling protocol, that encapsulates and encrypts network traffic. This process makes VPN traffic essentially opaque -- meaning unauthorized users can't detect the contents of the network -- as it transits the public internet. If a third party inspected traffic in transit, it wouldn't be able to access packet payloads.
VPNs prevent arbitrary third parties from inspecting traffic flow between specific users and the resources they access online. This is especially true for situations where employees use VPNs to protect work-related activities, transactions, file transfers, application use and more.
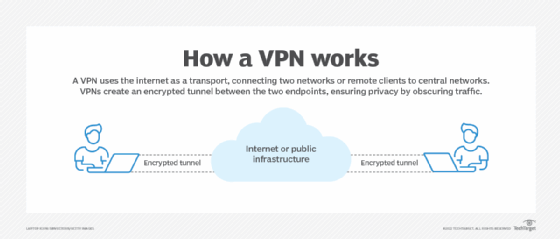
VPNs also hide specific user details in the traffic they protect. IP addresses, geographic locations, browser histories, devices and software are examples of information not readily available to those outside the VPN umbrella.
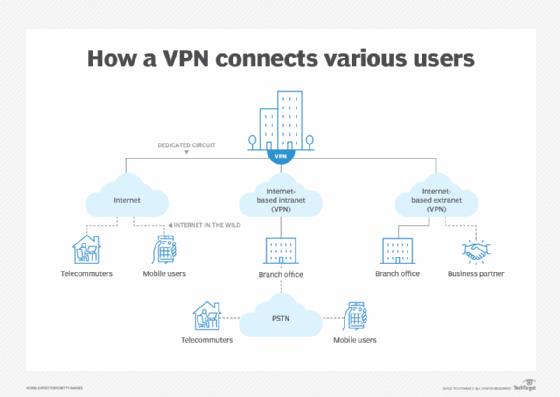
VPN use cases
Enterprises primarily use VPNs to overlay a secure, private network over the public internet. Typical use cases for VPNs include the following:
- Remote work. Organizations provide VPNs for remote employees to access network resources and applications.
- Privacy. Users and organizations that want to conceal work-related information, sensitive data and communications from third parties -- such as ISPs, telecoms and other companies that handle internet traffic -- can protect their traffic with a VPN.
- Security. Users who connect to the internet via an insecure network can use a VPN to secure their data and communications and avoid unwanted disclosures.
How to set up a VPN
Network admins need different elements at various steps when setting up a workable VPN, from the client, through the cloud, to the network boundary and into enterprise networks.
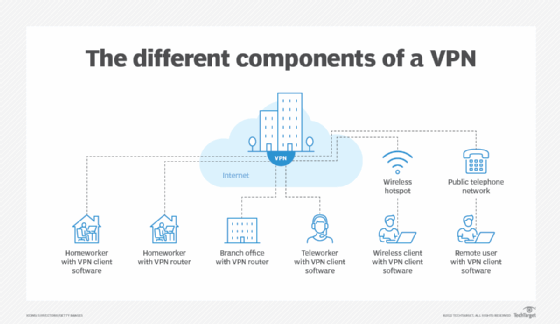
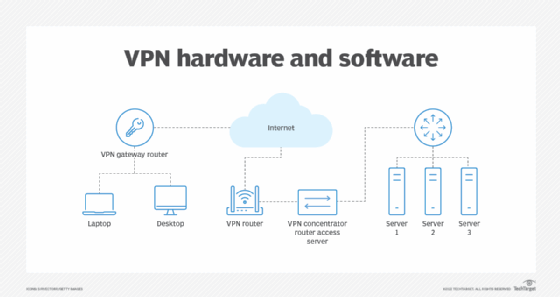
Basic requirements to set up a VPN include the following:
- Client VPN software. VPNs require client software to make secure remote connections. The clients must support the various applications and services users wish to access or run, such as collaboration tools, like voice and video conferencing.
- VPN infrastructure. Organizations must use specific VPN-aware routers and firewalls that permit legitimate VPN traffic to pass unhindered, while blocking unauthorized and unwanted third parties. These VPN devices typically use blocklisting techniques or address and domain name filters to enable this process.
- VPN appliance, concentrator or server. VPN appliances, concentrators and servers handle and manage incoming VPN traffic, as well as establish and manage VPN sessions and their access to network resources.
Some key design objectives to keep in mind when selecting VPN features include the following:
- secure remote access;
- easy setup, configuration and maintenance;
- affordability for widespread corporate use; and
- ease of use.
How to select a VPN
Choosing which kind of VPN to accommodate an enterprise network comes with its own share of difficulties. Network professionals are often caught between management dictates and user preferences when deciding which VPN to deploy, and this can pose some challenges for staff.
Look at user and platform preferences
Upper management typically chooses VPN designs based on a few criteria. Existing infrastructure dictates which new VPN components match compatibility requirements, and management might also base purchase decisions on the best price or optimal features-to-price tradeoff. Sometimes, however, management chooses a VPN due to a specific vendor choice or existing relationship.
When management follows this VPN design rationale, network and IT teams are rarely given the choice of which VPN to set up. They may have input into the selections, but their choice is subject to considerations and final selections from higher-ranking personnel.
Instead, organizations may want to adopt a bottom-up approach driven by users. In a user-driven approach, user platforms dictate VPN protocols and services, while low-cost or freeware VPN clients drive the remaining component choices.
A user-driven approach creates a free-for-all: Organizations can use multiple VPNs for different user groups or platforms. Ideally, the organization settles on a single choice or a limited number of choices, where network teams carefully balance security requirements against ease of use and productivity considerations.
Evaluate VPN client options
Choosing a VPN client involves considerations across a wide spectrum of capabilities and functionality:
- OS support. For those using PCs of some kind, it's best when a single client can support all OSes the organization uses. This consideration also applies to mobile OSes.
- BYOD. Organizations that support BYOD should also consider enabling VPNs for mobile devices, for both personal and work-related use. Even on company-provided devices, employees usually welcome this capability.
- Security and encryption. Broad support for remote access, tunneling and security or authentication protocols are key features to include when setting up a VPN. Some popular VPN protocol options include Secure Sockets Layer (SSL)/Transport Layer Security (TLS) and IPsec, as well as Remote Desktop Protocol or Layer Two Tunneling Protocol. Strong encryption support is also a must, with 2,048-bit Rivest-Shamir-Adleman encryption for key exchange and highly protected traffic and Advanced Encryption Standard 256 or better for all payloads and other traffic.
- Remote support and collaboration. The VPN environment should support remote access, remote virtual clients, assisted or interactive use for tech support, and collaboration among multiple parties for video conferencing. Ideally, VPN technologies integrate easily with existing infrastructures, runtime environments, applications, services and cloud platform investments.
- Price. Most organizations don't want to restructure their current ways of business to accommodate VPN use and prefer modest and inexpensive upgrades, rather than massive and costly changes. VPN price models are also important; higher-cost options generally offer more security, better integration, and easier maintenance and upgrades.
VPN deployment challenges
Learning how to set up a VPN correctly can help network teams avoid future complications. To prevent potential problems, network personnel must be aware of areas that could cause VPN issues and technical problems.
Below are some common VPN deployment challenges:
- VPN client software must work on all user devices, which can prevent VPN security breaches.
- VPN devices must also be compatible and interoperable with appliances, concentrators and servers.
- VPN protocols must work end to end through firewalls, routers and switches.
- Network teams must balance security and protection against ease and convenience to avoid technical VPN issues.
Countermeasures against VPN security risks
VPN technology offers specific and focused security technologies, but it can also be a magnet for attacks and exploits. In March 2022, the Infosec Institute reported that the rise of VPN use to enable the demand for remote access led to an increase in attacks. It is pivotal to secure a VPN to create a safe remote network experience.
The National Security Agency and the Cybersecurity and Infrastructure Security Agency recommend organizations follow some best practices for security that can minimize their attack surface when using a VPN. Some of those tips are the following:
- Choose a standards-based VPN that includes Internet Key Exchange and IPsec over options that use SSL/TLS. If a VPN uses a custom SSL/TLS tunnel as a fallback to standards-based operation, this option should be disabled.
- Set up VPNs with strong authentication and encryption algorithms and protocols.
- Use multifactor authentication (MFA) with two or more factors to increase security. Whenever possible, consider replacing password-based authentication with client authentication via certificates stored in smart cards or other hardware-secure storage.
- Curb vulnerabilities through regular patching, and maintain a current software bill of materials to ensure secure and updated code. Apply updates when they become available, and force password changes when exploits of known vulnerabilities are documented in the wild.
- Limit VPN access only to authorized users. This step might involve creating firewall rules to limit access on specific port addresses, such as TCP and User Datagram Protocol. Carefully manage and monitor inbound and outbound VPN access, with endpoints restricted solely to allowed IP addresses. Block VPN access to management interfaces so compromised admin credentials can't threaten network takeovers.
- Consider deploying VPNs within a zero-trust framework with network segmentation to enforce the principle of least privilege (POLP).
- VPN traffic should pass through a security stack on its way into and out of an enterprise network. This stack should include a web application firewall and intrusion prevention systems. Teams should also configure the VPN to enable all web application security settings -- to avoid replay attacks using expired user session data, for example.
A detailed approach to network security monitoring and maintenance enables a VPN to boost security and provide users with secure enterprise network access.
Best practices for setting up a VPN
Enterprises should set up standards-based VPNs that meet their users' platform needs. For example, a VPN can accommodate mobile devices and stationary devices, but all VPNs -- regardless of the device on which they run -- should support strong authentication and encryption. MFA is one way to implement secure remote access for users outside office locations. Network architects should closely monitor VPNs and update them to accommodate security updates, patches and fixes.
By itself, a VPN can't make remote access safe and secure. Network users should undergo security awareness training to avoid unsafe habits and minimize the risk of encountering online attacks. Network professionals should also carefully monitor the VPN and stay alert for anomalies or unusual access patterns to prevent attacks. For enhanced security, network professionals can consider limiting VPN access within a zero-trust framework that checks and limits IP and media access control addresses when necessary and enforces POLP for all use.








